Auditing Automated Environment – Understanding the Basics
Introduction
With increasing digitization and rapid adoption of technology, organizations have understood the need to enhance their cyber defenses, thanks to growing technology risks. This has resulted in organizations laying greater emphasis on their underlying Information and Technology Controls. While on one side, COVID-19 has accelerated the technology adoption, it has made also made virtual and hybrid working a reality. All these changes call for lines of defense to regularly review the risks pertaining to the underlying technologies and ensure it is within its appetite.
While the regulatory frameworks such as the RBI, SEBI or IRDA Guidelines, require organizations to periodical review these risks and report the same, it is equally important for all establishments to assess their “digital risk” in today’s era. Even a kirana store (your neighborhood grocer) who accepts digital payment via wallets or UPI is exposed to technological risks! From an audit perspective, the auditing standards require auditors to understand the underlying risks including the technological risks and take appropriate safeguard to assess those risks. Legislations like the Internal Control over Financial Reporting (part of the Companies Act, 2013), the Sarbanes Oxley Act, have mandated the management and auditors to comment on the design and effectiveness of internal controls. In this assessment often disregarded are the implications of technology and the technological risks. Financial Auditors also want to get comfort in the way the financial reports are being generated and if all information provided by entities (IPE) are generated after adequate checks and balances. All of these require technology to be designed and operate effectively. Thus, there is a need for auditing the Technology Controls, also known as IT Controls.
These IT Controls can be Application specific or embedded within an application called as IT Application controls (ITACs) or could pervasive across the organization or work behind the scenes of an application and are popularly referred to as IT General Controls (ITGCs).

ITGCs vs ITACs
IT General Controls (ITGC) [sometimes also referred to as General IT Controls (GITC)] are controls that apply to all systems, components, processes, and data for a given organization or IT environment. The objective of ITGCs are to ensure the proper development and implementation of applications, as well as the integrity of programs, data files, and computer operations, ensuring the access is restricted to those who are in need and to the extent which is required.
ITGCs also give assurance that the underlying IT system produces accurate results and reliance can be placed on the output of the system. ITGC audits are normally done as part of financial statements audits to review the controls in place for the IT systems that have a direct effect on the financial statements. ITGC audits could also be performed independently to assess the accuracy and integrity of the output of any system. They could be mandated by virtue of any regulatory requirements, as a part of corporate restructuring or due diligence exercise as well.
ITGCs should be clearly distinguished from IT Application Controls (ITACs) which predominantly focus on the controls in built into any application such as input controls, limit checks, validation, and integrity checks etc. It is to be noted that Application controls often are embedded within the Business process controls, such as controls in built in Procurement to Pay (P2P) or Order to Cash (O2C) etc. and give assurance for the underlying business processes.
To illustrate, assume an ERP has a feature where Invoices shall be automatically processed, on successful completion of 3-way match, i.e., only when the details as per Purchase Order, Goods Receipt Note and Invoice match or a Sales invoice can be raised only if the Sales Order matched with the Dispatch note, these are said to be Application Controls which ensure, the underlying business process, in this case the Procurement and Sales respectively, are in order.
On the other end, it is equally important to ensure that person having access to enter the above data is restricted and ensure appropriate segregation of duties are in place to avoid conflicts. This is achieved by restricting access to appropriate personnel and regularly reviewing the access granted. These controls over access are examples of IT General Controls.
Case Study:
An organization has 4 IT Applications namely SAP R/3 as ERP, HRMS for HR and Payroll operations, KOTS for managing Procurement and BILLSYS for billing and receivable management. All of these are hosted within the organizations servers located at Head Office. These are standalone applications and are all integrated with the ERP. Each of them has different Databases and Operating Systems and are well networked across the organization.
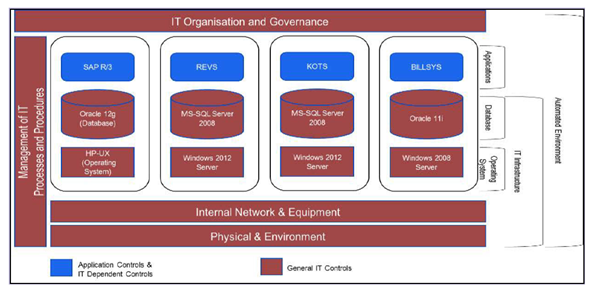
Fig 1: Illustration of the Organizations IT Environment and how IT Application Controls and General Controls operate
Given this set up, let us illustrate what could be the possible IT Risks:
- Risk of unauthorized access into the systems and network
- Risk of data loss or data theft
- Risk of operating system vulnerabilities (say Manufacturer not giving support to outdated Operating Systems) or risk of default credentials not modified in database
- Risk of unauthorized changes made to the Application or the Programs
- Risk pertaining to application interfaces
- Risk of unauthorized access to server room (physical environment)
- Environmental risks such as Fire, Humidity, Air conditioning etc.
- Risk of incorrect inputs given to the system owing to lack of mandatory checks and balances such risk of entering incorrect GST rate instead of not being chosen as a drop down or auto configured in BILLSYS
- Risk of incorrect processing logic, say HRMS calculating the salary incorrectly or KOTS incorrectly recording the logic of 3-way match.
- Risk of output generated incorrectly, say output not getting refreshed every time fresh entries are posted into the system, say the ERP is not generating the updated Profit and loss after passing audit adjustment entries.
In the above illustrations, risks 1 to 7 can be mitigated by ensuring appropriate IT General Controls are in place and risk 8 to 10 can be mitigated with appropriate IT Application Controls.
Concluding Thoughts
It is clear from the above that the role of IT controls is significant to get comfort on the underlying IT Infrastructure and to place reliance on the integrity, processing and accuracy of the processes and reports generated. The next interesting question as auditors is, how does one audit these controls? How can one ensure that the risks are under control? Well, let us explore them in our next article.
Author
The author CA Narasimhan Elangovan, is a practising CA and partner KEN & Co. He is a GRC Professional, a Digital transformation catalyst and an author. He believes in the power of technology to solve everyday problems. He can be reached at narasimhan@ken-co.in

